A Few Best Things About the New F5 Labs Site
With most F5-focused eyes squarely fixed on the global Agility conference last month, F5 Labs—the company’s threat research organization—was also making moves. While a couple enhancements are still under wraps, this article takes a look at some of the notable improvements to the site (F5Labs.com) and how the group’s web presence is evolving to better match the ways industry information is referenced, organized, and consumed.
Formally launched in January 2017 to gather global threat intelligence data, analyze application threats, and publish related findings, F5 Labs has further solidified the company’s security bona fides. This summer’s site refresh marks the first significant group of upgrades around the user experience and insights made available for F5 customers and the broader application security community.
So…What Are They?
Right, let’s get to it, starting with the obvious ones:
Overhauled Look-and-Feel – Is there anything worse than just reading plain text describing a refreshed visual experience (other than combining hyperbole with rhetorical questions)?
So, while we could undoubtedly use this space to expound on how it’s moved from grid-like arrangements to modern layering of design elements that make you feel more like you’re flipping through a graphic novel (in a good way) than sorting a research compendium, let’s instead do a Before-and-After on the homepage as a representative example.
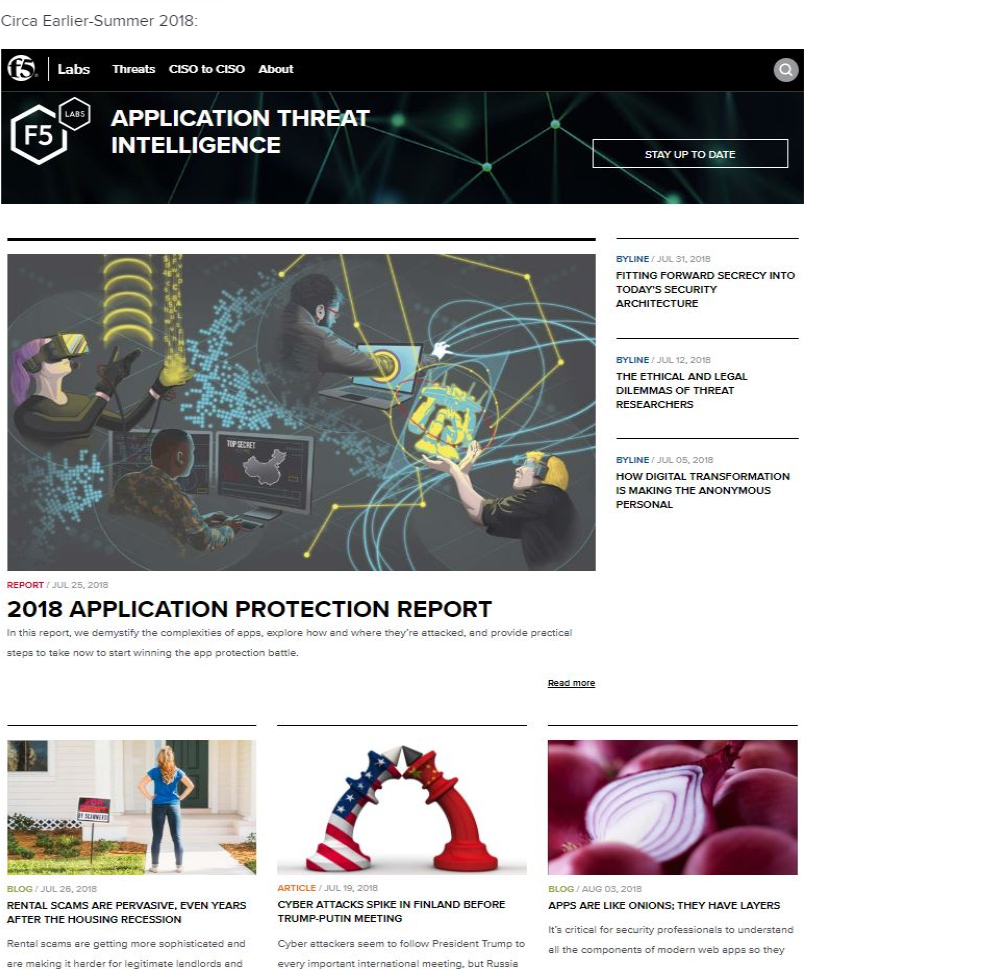
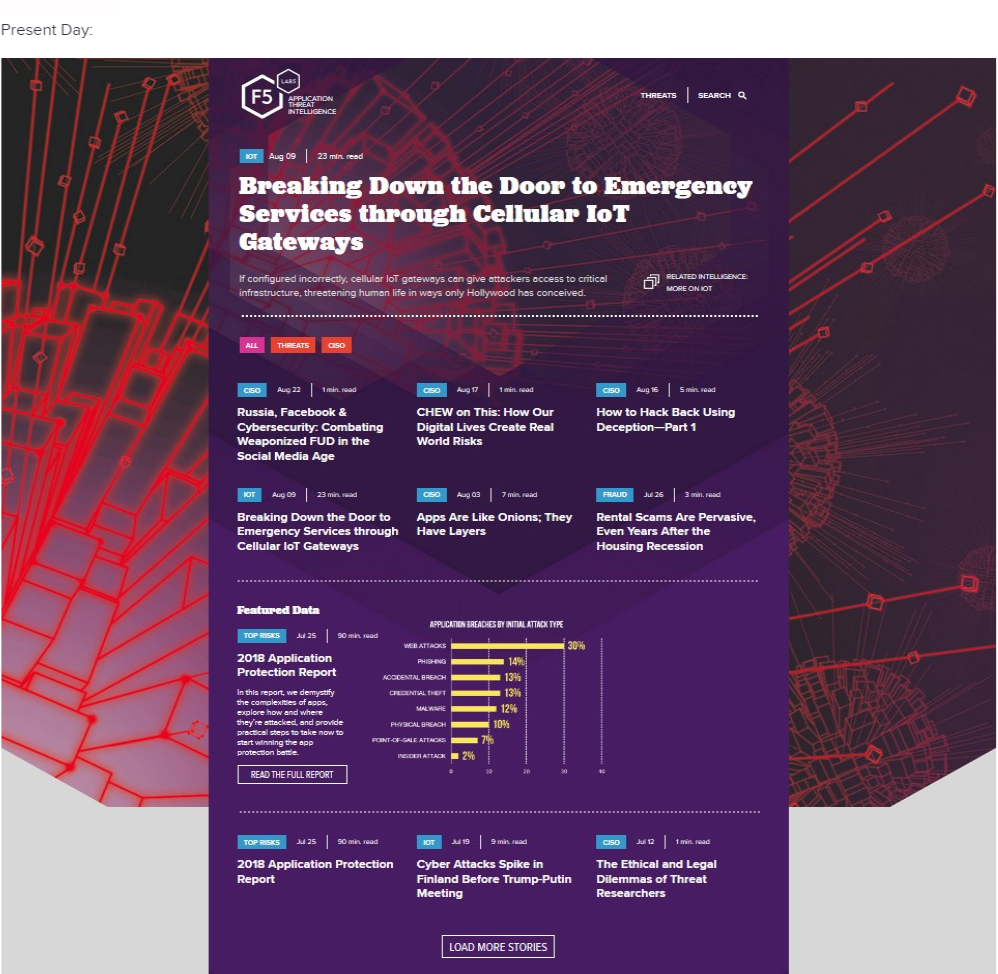
Besides better incorporating visual variety, the second is also a significant improvement for site visitors to easily find and consume content, which provides a nice segue to the next topic of emphasis.
Improved Site Navigation – Until recently—and as seen in the Before image—the way site materials were indexed largely centered on content type. While not without its advantages, this otherwise efficient approach has a few drawbacks. The main issue? When you’re looking for useful, actionable details, you don’t so much care if they can be found in a blog, article, byline, report, or elsewhere. You want quick access to the most helpful information and guidance related to a specific threat or topic.
With that more intuitive approach in mind then, the Labs team has revised and expanded its primary navigation around the most compelling items, such as Cryptojacking, Attack Campaigns, Fraud, Ransomware, IoT, and CISO topics.
Additionally, each content piece now has a set of “Vitals” associated with it, such as the application tier impacted (more on this in a minute), attack type, attack method, vulnerabilities targeted, the exploit ID (if one exists), type of malware used, attack campaign name, and attack motive. In other more conversational words, all the types of information a security professional needs to understand if a specific threat impacts their organization, and if so, the potential likelihood and severity of impact.
With this level of aggregation, you can quickly get more granular regarding attack types and remediation specifics without needing to sift through a single, somewhat amorphous “Threats” area.
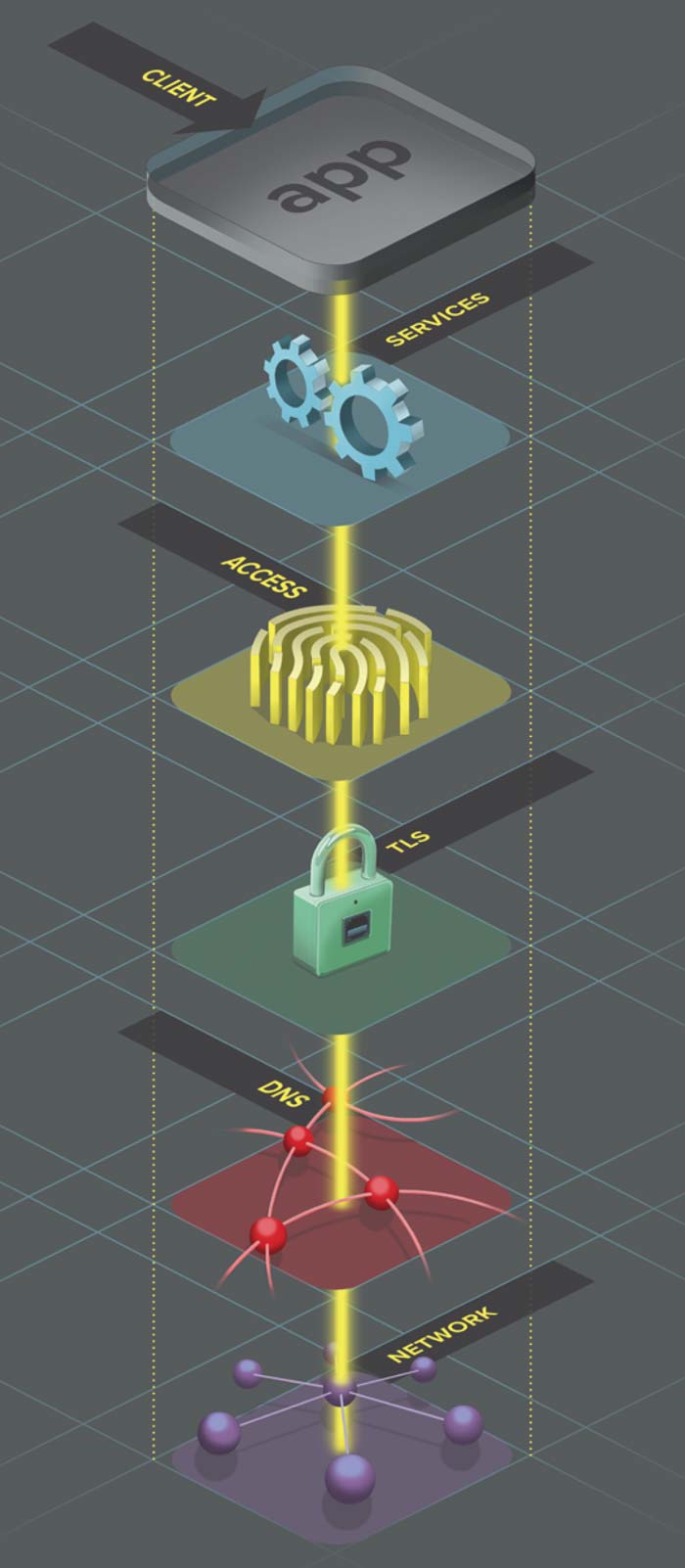
Content Discoverability – OK, this sounds conspicuously similar to the point above, but stay with us. First, some establishing context… If you’ve read the recent 2018 Application Protection Report, you know that it’s thorough. You may also recall this particularly effective description of apps:
“Web applications are ‘colony creatures.’ They consist of a multitude of independent components, running in separate environments with different operational requirements and supporting infrastructure.”
Accordingly, to better quantify and categorize the different type of application threats, the report examined application threats specific to a defined series of interacting tiers, each having its own characteristics and specific vulnerabilities (shown at right).
Why is this important? Well, in a prime example of an organization practicing what it preaches, eating its own dogfood, drinking its own champagne (did we miss any?!), the Labs team has organized areas of the site in line with this framework. That means that you can find information about certain types of attacks through an area of the site that visually corresponds to the section of the security stack targeted by a particular attack. Let’s hit that point again: you can now get threat intelligence based on where and how specific threats impact applications. Very cool.
For example: Curious about cross-site request forgery? Check out the Client-Side Attacks area. Concerned about DNS cache poisoning? You’ll find that with the App Infrastructure Attacks. In addition to giving you quick access to desired intel, this approach also outlines the breadth of attacks tied to each area of your valuable infrastructure, helping you visualize what you want to protect and what you need to defend against. Because if you don’t understand where an attack impacts your assets, you can’t protect apps, data, and users appropriately.
[Author’s note: I’m reminded that this is only one method of finding information on the site, and F5 Labs features myriad ways to quickly surface the most relevant information for users. This is just one of the newer ones…]
Some Other Cool Things on the Way
Since we’re dangerously close to overshooting best-practice article length, we’ll cover these next points quickly, identifying other enhancements on the roadmap:
- Improved author bios better introducing the people behind the perspectives on today’s most persistent and immediate threats.
- Content personalization to automatically find and surface materials most relevant to users’ site interactions and areas of interest, along with recommended preventative actions to take.
- Enhanced media throughout the site, highlighting things like heatmaps, graphs, charts, diagrams, and videos in the context of particular threats and attack trends. And yes, as you may have seen (heard?), the team has recently even dipped their collective toe into podcasting
As you’d expect, there are a number of other nice touches peppered throughout—such as a cleaner search interface—that can be found simply by looking around F5 Labs. But that’s enough for now if we’re going to keep this to a triple-digit word count. So enjoy the new site, and stay up with latest threats, attacks, and related content via Twitter and LinkedIn. Until next time…
