Volume 2: API Authentication Incidents
The second volume of the 2020 Application Report explores how API authentication goes wrong, what happens when it does, and what you can do to make sure it doesn't.
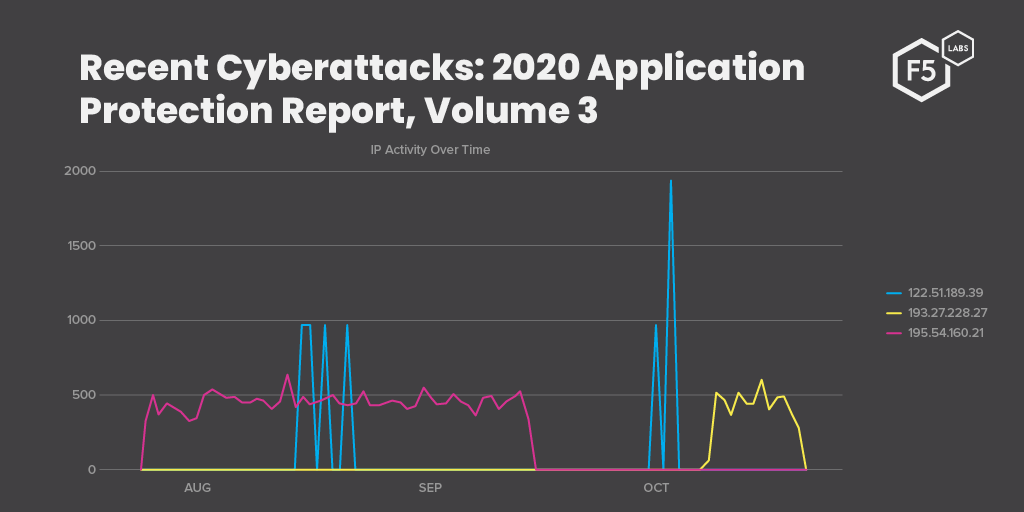
Applications have become the focal point of the Internet, the workhorses behind organizations of all types. Attackers have figured this out, and they target applications more than anything else (besides people). This research series ties together trends and data from a number of perspectives to give an overall picture of the application security threat landscape.
Click through the animations below to understand how different attacks unfold.