Securing Identity for Office 365
Microsoft Office 365 is a popular choice when you’re looking to outsource the management and infrastructure costs of running commodity applications like email and other productivity tools. Office 365 enables the use of a federated identity model that gives you full control of a user’s identity, including their password hashes.
Using BIG-IP Access Policy Manager (APM) lets you to provide secure, federated identity management from your existing Active Directory to Office 365, without the complexity of additional layers of Active Directory Federation Services (ADFS) servers and proxy servers. You can use many of the enhanced APM security features, such as geographical restrictions and multi-factor authentication, to further protect access to Office 365.
Once you’ve decided to migrate users to Office 365 you’ll need to decide on a sign-in model. Many large organizations choose a federated identity model, so they can retain complete internal control of password hashes.
In the federated identity model, Office 365 uses Security Access Markup Language (SAML) to authenticate users using your existing Active Directory service (the Identity Provider or IdP). Choosing the federated sign-in requires that you allow Office 365 to access your Active Directory servers and to translate SAML authentication requests.
One way to accomplish this is using Microsoft Active Directory Federation Services (ADFS) servers and ADFS proxy servers to manage secure access and act as the SAML IdP.
But there’s an easier way.
With BIG-IP Local Traffic Manager (LTM) and Access Policy Manager (APM), you can eliminate either just the ADFS Proxy servers or the ADFS proxy servers and the ADFS servers themselves. In either case, the advanced security protection policies that BIG-IP offers (firewall capabilities, geographical, reputation restrictions, pre-authentication, and others) can be used to protect your key directory infrastructure.
Replacing the ADFS proxy servers gives you high availability as well as pre-authentication services for the ADFS servers, provided by a secure, firewall-certified platform.
Replacing both the ADFS proxy servers and the ADFS servers themselves provides the same security and pre-authentication benefits, plus it simplifies the infrastructure.
Clients can be pre-authenticated with advanced checks such as two-factor authentication, client certificates etc. You can also deploy endpoint checks, such as location and reputation.
Deploying BIG-IP to protect or replace ADFS servers can be greatly streamlined by using the F5 ADFS iApp template. iApp templates transform the creation of advanced configurations into a simple, wizard-driven process that results in a tested and verified config.
Once you have a working SAML IdP, you can extend this identity federation to many other SAML-enabled applications and services, giving you single sign-on across many other web-based SaaS applications.
First, you’ll decide which deployment model to choose. Your options are fully laid out in the F5 article series on ADFS.
1. Once you’ve decided on a deployment model that meets your requirements, read the ADFS Deployment Guide and download the iApp Template.
2. Make sure you have the credentials and permissions to make config changes to your Active Directory servers.
3. Deploy your BIG-IP Systems and test high availability, network connectivity, and so on.
4. Run the iApp template and enter the required information. Now you have a basic working installation.
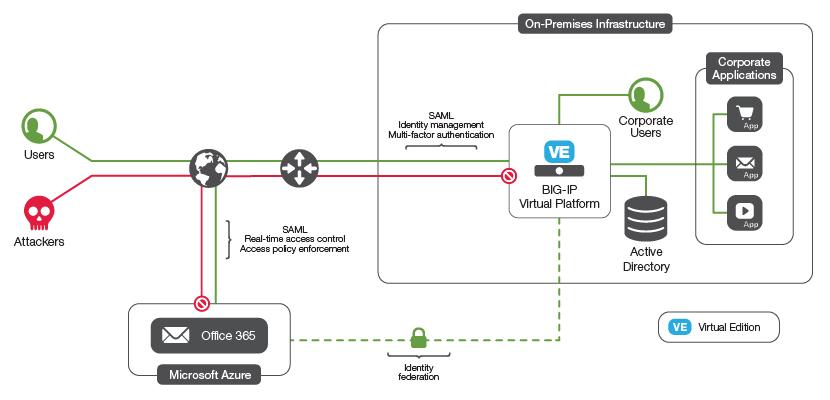
Streamlined, secure, and managed access for users to Office 365.
If you want to explore advanced authentication, read BIG-IP Access Policy Manager Policy Manager: Authentication and Single Sign-On.